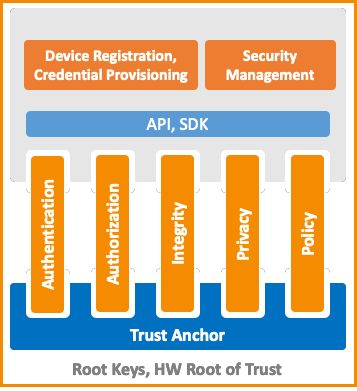
The challenge of trust and device identity
In many cases within the IoT, the old approach of verifying device identity alone is not enough. The device may, for example, only be trusted if it is both verified and in a certain location, at a certain time. A specialist IoT trust layer, therefore, needs to account for multiple key attributes as per the security policy of each specific device and its association to the application.
To further compound the problem is the operational complexity of provisioning and managing the trust layers at IoT scale – even if the right security protocol is available. Any IoT security framework needs to enable easy automation.
The biggest change and challenge in the IoT is device identity. While advances are being made in some aspects of traditional identity management using username/passwords, X.509 and SAML certificates, these methods are still inadequate and rarely address IoT use cases for identity.
A common problem is how to provision and bind the identity to the device, and how to securely manage it as per policy.